Configuring Oracle OIF for Salesforce.com SAML SSO
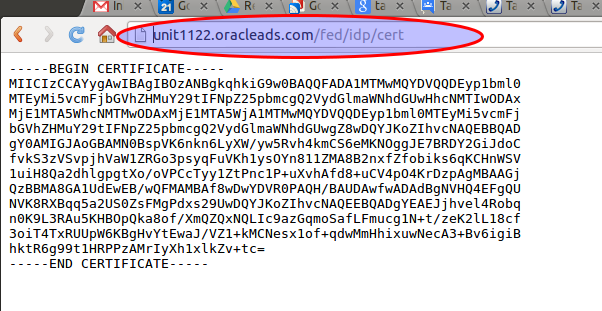
Here is a quick how-to on configuring Oracle Identity Federation (OIF) as the SAML Identity Provider for Salesforce.com. This turns out to be surprisingly easy to set up. For pre-requisites you should have the following in place: It is easiest if your OIF instance is configured to use POST SAML bindings by default. You can override this on a provider basis but most often you will use POST, so it makes sense to set it as the default. You need a salesforce.com account. Developer accounts are free and support SAML. Create a user in your ldap for testing SAML SSO. We will match on the users "mail" attribute. Set this to a relevant value (testuser@example.com). The mail attribute does not need to match the salesforce.com account id. This example assumes we are using OAM as the authentication engine for OIF, and they both are referencing the same ldap server. Step 1 is to import your OIF IdP cert into salesforce.com. The cert is available at http://e...

